In the realm of cloud security, controlling who can access your cloud resources and what they are allowed to do is paramount. AWS Identity and Access Management (IAM) is the foundational service in AWS that enables precise and secure access control to resources.
IAM provides various identities and policies to manage authentication, authorization, and permissions within an AWS environment, ensuring only authorized entities operate within the cloud infrastructure.
Introduction to AWS IAM
IAM allows organizations to manage users and their permissions systematically. It enables secure access through identities like users, groups, and roles, each serving distinct purposes in granting and controlling access to AWS services.
With IAM, security is customizable, scalable, and aligned with the principle of least privilege—users get only the permissions necessary to perform their tasks, thus reducing security risks.
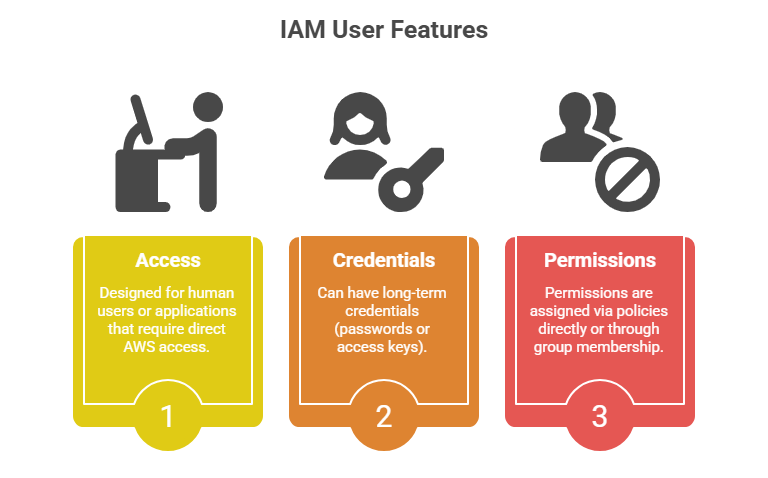
IAM Users
An IAM user represents an individual person, application, or service that interacts with AWS resources.
Each user has a unique identity with credentials such as passwords or access keys, which allow them to sign in and make requests to AWS services.
By default, new users have no permissions and must be explicitly granted access via policies.
IAM Groups
Groups are collections of IAM users and provide an efficient way to assign permissions to multiple users at once.
Instead of attaching permissions individually to each user, administrators assign policies to groups, and all users in the group inherit those permissions.
Important details on IAM groups:
1. Simplify permission management for multiple users with similar roles
2. Users can belong to multiple groups simultaneously
3. Groups themselves cannot have permissions; only policies attached to groups grant permissions
4. Groups cannot be nested inside other groups
IAM Roles
IAM roles are identities created to be assumed temporarily by trusted entities such as AWS services, users from other AWS accounts, or federated users.
Roles are ideal for granting temporary permissions without sharing long-term credentials. They are commonly used for service-to-service interactions, cross-account access, and automation tasks.
Characteristics of IAM roles:
1. Provide temporary security credentials via AWS Security Token Service (STS)
2. Consists of trust policies defining who can assume the role and permission policies defining allowed actions
3. Enhance security by eliminating the need to store credentials in code or on servers
4. Can be assumed by AWS services like EC2, Lambda, or by IAM users and external identities
IAM Policies
Policies are JSON-formatted documents that define permissions by specifying allowed or denied actions on AWS resources. Policies can be attached to users, groups, or roles, and are the mechanism by which AWS enforces access control.
.png)
Policy Elements Include:
1. Effect: Allow or Deny
2. Action: The AWS service operations permitted or denied (e.g., s3:GetObject)
3. Resource: The specific AWS resources the policy applies to, referenced by Amazon Resource Names (ARNs)
4. Condition: Optional criteria for when the policy applies, such as IP address restrictions or MFA requirements
